If you are spending $10k per month or more on Google ads, you need to know this:
You could lose up to $15,000 this year due to Click Fraud. 💸
And you’re not alone:
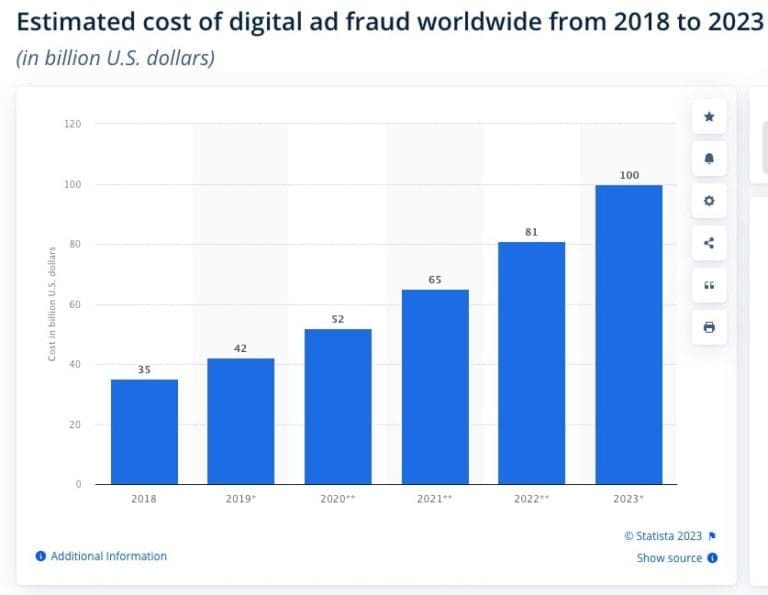
Forecasts predict ad fraud costs to rise from $19 billion in 2018 to $100 billion by 2025, highlighting the escalating challenge for advertisers and agencies.
At Inceptly, we recently assisted a client in the Lead Gen Space, grappling with the issue of fake leads and traffic. Our path to successfully addressing this issue intensified our curiosity about the roots of digital fraud and what hard-working marketers can do to mitigate and avoid it.
Is there a way to 🛑 STOP 🛑 click fraud?
With the right fraud prevention system, you can prevent the vast majority of click fraud.
But “plug-and-play” solutions are hit or miss at best. At Inceptly, the custom anti-click fraud systems we’ve built for our clients have helped save thousands of dollars in wasted spend per month.
Want to get our 1-on-1 advice on how you can stop wasted adspend & fight click fraud using the latest custom fraud-fighting setups?
Click the button to set up a Free Click Fraud Prevention brainstorm call with our team:
Recall the time when Google confronted the notorious “Clickbot.A”—a vast botnet of 100,000 machines governed by an HTTP-based master? Google’s meticulous investigation and subsequent case study on Clickbot.A remain invaluable. In this piece, we’ll journey through Google’s battle against Clickbot.A, offering insights that might redefine our perspective on online advertising security.
But before we explore this intriguing case study, let’s set the stage with some cautionary statistics:
- approximately 90% of all pay-per-click (PPC) advertising campaigns on Google and Bing are currently vulnerable to the threat of click fraud.
- 90% of PPC campaigns are susceptible to click fraud, costing advertisers $81B last year alone.
Google's Deep Dive Into Clickbot.A's Deceptive Mechanisms
Clickbot.A was not your average botnet. It was a “low noise” fraud machine, carefully mimicking real user behavior.
The Clickbot.A creators clearly invested time in making their system seem genuine. But Google’s security teams proved you can uncover even carefully hidden fraud.
By reverse engineering Clickbot.A, Google discovered how it worked:
🟦 The botnet pretended to be a legitimate publisher able to display Google ads
🟦 Behind the scenes, it programmed infected computers to click on ads automatically
🟦 These fake clicks aimed to generate fraudulent ad revenue for the bot creators
Before we continue, just a quick reminder:
🚩 What is click fraud?
Click fraud refers to malicious and fraudulent clicking on online ads with the intent to generate false interactions and drain ad budgets. It involves the use of automated scripts or bots that mimic human behavior to click on ads, leading to inflated click counts and wasted advertising dollars. Click fraud can occur in various forms, such as ad fraud, where website operators drive fraudulent clicks on their own PPC display ads, or when scammers target PPC ads on web properties they don’t own to cost advertisers money.
Click fraud can be perpetrated by individuals, click farms or automated bots like Clickbot.A.
The motivation behind click fraud can vary, including financial gain, sabotaging competitors, or manipulating search engine rankings.
👤 What is a clickbot?
A clickbot is a software robot designed to carry out click fraud. These bots are programmed to visit web pages and click on specific links, mimicking the behavior of human users. While some botnets can be purchased, others are malware that infects machines and operates as part of a larger botnet. Botnets receive instructions from a central command server on what ads to click, when to click them, and how often.
Clickbots can be categorized into two types: for-sale clickbots and malware-based clickbots. For-sale click bots, such as Lote Clicking Agent and FakeZilla, can be purchased online. They often use anonymous proxies to generate traffic with IP diversity. However, these click bots are relatively easy to detect and identify. On the other hand, malware-based click bots infect machines to achieve IP diversity, making it harder to differentiate their traffic from legitimate users. They can be more sophisticated, replicating human-like behaviors such as mouse movements, random pauses, and timing variations between clicks.
A Ploy to Siphon Google Ad Profits 💰
To understand how Clickbot.A tried to steal some of the advertising money, it is important to know how search engines like Google make money from advertising:
- Search – Search engines like Google provide a free service to search the internet. They make money by selling ads. Advertisers pay every time someone clicks on their ad. This is called pay-per-click or PPC advertising.
- Syndication – Google allows other smaller search engines to show its ads, too. These “syndicated” search engines get a cut of the ad money when their visitors click on the Google ads.
- Subsyndication – Some syndicated search engines share Google ads with even smaller websites. These “subsyndicated” sites get a small cut of the cut that the syndicated engine gets.
- Referral deals – Websites can also make money by referring traffic to certain sites like Google. If a user clicks from that website to Google, the referrer gets a small payment.
- Landing pages – When a user clicks on an ad, they go to the advertiser’s “landing page.” This is where the advertiser hopes the user will buy something and make the ad profitable.
So, the Clickbot.A botnet pretended to be a syndicated search engine sending users to Google ads. But really, it just faked the clicks to try to steal some ad revenue for itself.
Clickbot.A posed as a sub-syndicated engine under larger publishers, meaning a cut of the fraudulent profits would go back to Clickbot.A’s operators.
An Inside Look at How Clickbot.A Worked

A fascinating case study from Google provides rare insight into how cybercrime groups architect sophisticated click fraud operations. Researchers comprehensively mapped out how the stealthy Clickbot.A botnet functioned.
Here’s an inside look at how it worked:
🤖 Clickbot.A Anatomy
The botnet consisted of infected client computers (“bots”) and a central command and control server (“botmaster“).
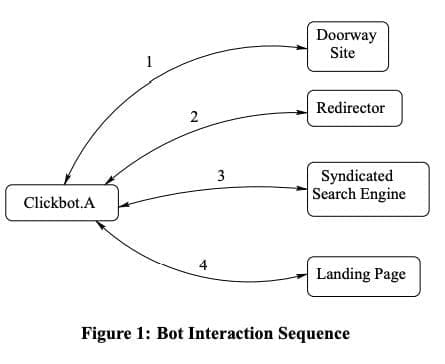
The botmaster issued instructions to the bot clients over HTTP. When bots visited the botmaster website, they would receive commands to visit “doorway” websites set up by the botnet operator. These doorway sites appeared to be legitimate publishers that could display ads.
From the doorway sites, the bots were shuttled through “redirector” websites to mask their origins further. Eventually, bots landed on pages containing Google ads and clicked on them, generating fraudulent revenue.
The botnet infrastructure with doorway sites, redirectors, and syndicated pages made the source of clicks difficult to trace. This allowed the botnet to conduct “low noise” fraud that tried to hide its activity.
🚪 Doorway Sites
A key innovation of the stealthy Clickbot.A botnet was the use of an entire network of fake publisher websites to disguise the source of fraudulent clicks. The botnet operator set up these doorway sites to appear as legitimate publishers that could display ads.
Each doorway site functioned like a simple search engine. It had a search box where bots could enter keywords provided by the botmaster. The site would return fake “search results” pages containing links.
These links on the doorway sites would ultimately lead to pages with Google ads when clicked by the bots. The botnet operator profited if the bots clicked on the ads.
The doorway sites allowed the botnet to pose as a real sub-syndicated search engine business. This lets them sign up for ad syndication deals to access Google ads.
Having many different doorway sites made it harder to trace back the source of the fraudulent clicks. If one site was detected, the operator could simply switch to others.
↪️ Stripping “Referer” Info
The Clickbot.A botnet utilized another clever trick to hide the fraudulent source of its clicks – routing traffic through legitimate redirector websites. These intermediary sites concealed the doorways where clicks originated.
After bots clicked links on the doorway sites, they passed first through redirectors rather than straight to Google ads. The redirectors would forward the bots onto syndicated search pages.
These redirectors eliminated the “referer” info, making the source of the clicks hard to trace. This obscured the associated doorway source and made the traffic appear more organic.
Without referrer data, ad networks could not easily trace the clicks back to identify Clickbot.A’s doorway sites. The botnet took advantage of how redirects naturally cause referer info to drop.
Blending fraudulent clicks with legitimate redirect traffic made the botnet more difficult to detect. Redirectors have many normal web uses beyond botnets.
📄 Syndicated Search Pages
A clever aspect of how the Clickbot.A botnet conducted stealthy click fraud was leveraging Google’s own syndicated ad network. The bot operators infiltrated the system by posing as publishers.
Google allows other search engines to display its ads and share revenues through publisher partnerships. Clickbot.A took advantage by registering its fake doorway sites as sub-syndicated engines under larger publishers.
When the infected bots clicked on Google ads within this syndicated search network, it generated money. A portion of profits from the fraudulent clicks would flow back to Clickbot’s “publisher” doorways.
Blending the fake clicks with real syndicated traffic helped the botnet avoid detection. The clicks appeared organic rather than originating from an abusive bot army.
By mirroring genuine publisher relationships, the botnet found a way to monetize clicks from 100k infected machines.
💸 Tracing the Money

A key aspect of identifying and disrupting major ad fraud schemes is following the money trail to uncover who ultimately profits. Google followed this money trail back through the network of fake doorway websites and syndicated search engines, all the way back to Clickbot.A.
When infected bots clicked on Google ads within the syndicated search network, ad revenue was generated. Google paid a share of this money out to partnered sites hosting the ads.
These syndicated search engines then passed a portion of earnings to Clickbot.A’s network of fake doorway websites that supposedly supplied the traffic.
By posing as sub-syndicators, the doorways received payments from larger publishers above them in the food chain. This money ultimately made its way back to the true botnet operator.
💥 Estimated Damage
Had it not been caught, Clickbot.A had the potential to siphon off around $50,000 in ad revenue. While $50K may seem small, the architecture could easily scale, turning it into millions.
Analysts estimate that with 100,000 infected computers under its control. This projection assumed each bot could produce 10 clicks per day, with an average value per click of 5 cents based on Google’s ad rates. Of course, not all clicks successfully triggered payments.
Google invalidated all fraudulent clicks and banned syndicated partners showing suspicious behavior, effectively neutering the botnet.
⏳ Dynamic Adaptation
The botnet could even update its own configuration to dodge detection methods. This allowed the botmaster to tweak tactics regularly.
The centralized botnet server could securely push out new instructions to infected machines on the fly using encryption and authentication checks.
Some examples of parameters the botmaster could remotely reconfigure included:
- Doorway pages the bots should visit
- Syndicated accounts to funnel clicks through
- Timing and volume of clicks
By frequently changing these details, Clickbot.A avoided creating obvious repetitive patterns that fraud systems could easily spot.
The infected computers would passively pull down the latest configs when connecting to the botnet server. This enabled swift, centralized control without manually updating all bots.
The agility to retool itself allowed Clickbot.A to react faster and stay under the radar as platforms strengthened defenses over time. Botnet flexibility is vital to sustaining operations.
🤔 A Test Run for Bigger Botnets?
Some suggest Clickbot.A was a prototype, testing waters for more advanced botnets.
Several signs indicate that:
1️⃣ The bot and botmaster software used version numbers like 0.00X, typical for initial alpha test releases. More mature releases use versioning like X.Y.
2️⃣ Some botnet features appeared unfinished, like the lack of geolocation data in the botmaster console. This suggests development was still ongoing.
3️⃣ The botnet code contained vulnerabilities like SQL injection flaws. A more hardened, mature botnet would likely not have such obvious weaknesses.
4️⃣ The embryonic version numbers, incomplete features, and lack of security hardening all imply Clickbot.A was not yet fully developed and was still in the testing phases.
Botmasters often release a prototype botnet first to test concepts before building out a more robust version.
📈 Carefully Growing Botnet Footprint

According to Google’s analysis, the Clickbot.A botnet exhibited steady but controlled growth patterns, expanding from 100 to over 100,000 infected machines within just over a month.
Unlike worm attacks that spread wildly like Blaster and SQL Slammer, Clickbot.A’s growth was slower since it required direct attacker oversight rather than autonomous rapid propagation.
The operators used a Trojan horse disguised as a game to infect computers with Clickbot.A malware. This allowed targeted infections rather than mass spam blasts.
Researchers also believe the creators leveraged existing botnets by paying or bartering with their operators to distribute the Clickbot.A code to already infected machines.
Once infected, these computers became part of the botnet, receiving commands from a central ‘botmaster’ server.
The managed growth patterns allowed the botnet to scale up while avoiding triggering alarms by sudden rapid infection spikes. Tactical use of other botnets accelerated expansion.
🌎 Geographic Sphere of Influence
By analyzing the IP addresses of computers infected by Clickbot.A, researchers could map out the physical footprint of the botnet across the globe.
Researchers obtained tens of thousands of IP addresses of machines infected by Clickbot.A. Analysis showed the IPs were globally distributed, with infected machines located around the world. There was almost no overlap with known open proxies, implying the machines were compromised hosts rather than just traffic relays.
The IPs correlated strongly with email spam blacklists, suggesting the infected machines may have also been part of spam botnets.
This indicates the Clickbot.A botnet overlapped with and leveraged infrastructure from other criminal botnets focused on spam distribution.
🪤The Cat-and-Mouse Game Between Stealthy Botnets and Ad Platforms
Instead of attacking top search engines directly, Clickbot.A spreads its clicks across various ad networks to look organic. This hides their activity but reduces earnings on each platform. To profit, they have to target multiple sites subtly.
When ad platforms spot suspicious clicks, they can just cancel them without telling the botnet owners.
To stay ahead, ad systems need smart tools to find hidden fraud that normal click logs don’t catch. Missing fraud hurts advertisers’ returns on investment (ROI).
Measuring ROI helps justify ad spending and improves fraud detection. But botnets adapt with trickier techniques.
It’s a never-ending game. As botnets get smarter, ad platforms must keep evolving their fraud detection and show the value of ROI to keep advertisers happy.
👉 For a deeper dive into Clickbot.A, HERE’s Google’s own research.
🕵🏻♂️ Invalid Traffic & Click Fraud Stats

Current research shows that click fraud is still a serious threat to advertisers and agencies:
- Approximately 38% of web traffic is automated/bots. Of these bots, 24% are considered ‘bad bots’ or bots used for fraud and theft
- On paid search campaigns, an average of 14% of all clicks are from non-genuine sources (click fraud)
- At least 15% of paid web traffic is un-attributable, most likely lost to fraud
- 90% of all PPC ad campaigns on Google and Bing are affected by click fraud
- Rates of click fraud jumped 21% during the initial stages of the Coronavirus pandemic
- Industries with the highest rates of click fraud include photography (65%), pest control(62%), locksmiths(53%), plumbing(46%), and waste removal (45%)
- Financial and legal services were hit by around 25% invalid traffic/fake clicks during 2020
TL;DR
Click fraud is an intricate, evolving problem. The case of Clickbot.A provides valuable insights into its complexities:
👉 Diligent investigation and disruption of sophisticated botnets can successfully prevent fraudulent clicks and wasted ad spend.
👉 By tracking the money trail, invalidating fraudulent clicks, and banning abusive syndicated partners, Google was able to nip a sneaky click fraud scheme in the bud before advertisers were harmed.
👉 With click fraud continuing to grow and now extracting up to 15% of paid web traffic, advertisers and agencies cannot rely on platform fraud detection alone.
👉 The latest statistics show that most PPC campaigns are still vulnerable, with nearly $100 billion estimated to be lost annually by 2025.
That's why at Inceptly, we design custom strategies to protect our clients from bots and counterfeit traffic, ensuring optimal ad performance.
Want more content like this?
Don’t miss out on the latest news and updates from the world of Direct Response advertising! Subscribe to our newsletter today 👇

Jelena Denda Borjan, Staff Writer
Drawing from her background in investigative journalism, Jelena has an exceptional ability to delve into any subject, no matter how complex, dig deep, and present information in a clear and accessible manner that empowers readers to grasp even the most intricate concepts with ease.
Fight Click Fraud & Stop Wasting Adspend
With the right fraud prevention system, you can prevent the vast majority of click fraud. But “plug-and-play” solutions are hit or miss at best.
At Inceptly, the custom anti click fraud systems we’ve built for our clients have helped save thousands of dollars in wasted spend per month.
Want to get our 1-on-1 advice on how you can stop wasted adspend & fight click fraud using the latest custom fraud-fighting setups?
Click below to set up a Free Click Fraud Prevention brainstorm call with our team
Like this post? Let's continue the conversation!
Get in touch with us by shooting us a quick email or tagging us on LinkedIn or Instagram, and sharing your thoughts. Your feedback helps us keep our blog relevant and interesting.
Get Our Newsletter
Need Help?
Get in touch with us for an insightful evaluation of your ads + actionable tips to help amp up your direct response revenue